ThunderSoft DRM Protection Activation bypass + Key Full Version Free Download

ThunderSoft DRM Protection 5.0 Activation bypass is a DRM solution for video/audio/image/document files. DRM-protected media files can prevent illegal copying and distribution; Unauthorized users cannot open them. The authorization key can be bound to the end user’s hardware, a device, a key, the time range of which can be specified, and the blacklist function is also included. Our software offers custom watermarks, custom player and many other advanced settings to help you with complete DRM protection.
ThunderSoft DRM Protection Full Version is a new and powerful audio and video file closing program with powerful features. They know that all information can be shared online today. Digital recorders, a collection of digital images or popular video files (music, lecture or two), are the most commonly used electronic formats. The ease of communication and the availability of diverse users have allowed people to share information with friends online or in different ways without having to copy it. For example, if you run a course, you need to ensure that only participants see what is presented to you or your organization.
If you share files with customers who don’t share files, there is a risk that each customer can share valuable resources for free. The software we are talking about in this article allows users to convert all types of files such as photos, music or videos to other colors for access. The only one who will allow you to get away! This feature allows the content (KSEE) of User Content to be modified to make it available to customers by entering a password, dongle or other security feature.
ThunderSoft DRM Protection is a DRM solution for video/audio/image files. Media files are protected by DRM and can prevent illegal copying and distribution; Unauthorized users cannot open them. Block permissions can be associated with the end user’s hardware, a block, or a device. You can specify the period and the blacklist function is available. ThunderSoft DRM protection software offers watermarks, custom players and many advanced settings to help you with complete DRM protection.
Security Password Maker allows you to create multiple passwords for multiple users. A system has been provided that allows people to discuss details online or send them to multiple friends in various ways, regardless of whether they are connected. For example, if you’re an instructor, it’s important to make sure only viewers can see articles paid for by your company. The change from Open Sesame may be due to different manipulators using secret code creators. You can purchase custom theater supplies. The guarantee code supports mobile or media printing.
The software we test for you provides users with these gadget deals. Exploring it and acting on it is only possible in the societies that allow you! The application can redesign its executable design (EXE) so that it can only be opened using the keywords “essential hardware” and “sanctuary” methods intended for its actual consumers. The key to the agreement can be mandatory with the end-user hardware, a strategic maneuver, the time interval and the opt-out function.
ThunderSoft DRM Protection software sends personalized impressions of a conference participant. It is maintained even without pay by your employer’s benefit limit, and often people with CPU culture do not imply that they have the right to use this most popular type of software. In Productivity Resolution, be sure to navigate to a folder in GEM Settings. This is a high-end radio design that is threatened by DRM and uses unusual face-to-face encryption. With this plan, you can protect all your documents as innocently as you can imagine.
Features & Highlights:
- Allow combining multiple files into one DRM protected file.
- Encrypt media files with Advanced Encryption Standard (AES) and provide excellent security.
- High-speed encryption and the output file can be opened quickly.
- Allow the authorization key to connect to a computer, USB hard drive or CD or not.
- It allows you to add watermarks, supports floating style or fixed watermark.
- Copy protection settings can prevent screen recording software from playing and prevent playback while connected to the Internet.
- Ad Settings allows you to add ad links to DRM-protected files.
- The online password blacklist can be used to disable the password sent to users.
- With the password creator you can create different passwords for different users.
- Enable personalized players with your company information.
- Avoid screen recordings and screenshots from most online screen recorders.
- Combine multiple files and create a secure file.
- Multimedia content is the highest algorithm.
- Feel free to make the code available to the public.
- It can be rotated in different ways.
- Learn how to change objects using methods such as images.
- Ability to passwords on the Internet.
- Quickly and easily create passwords for multiple users.
- Inside are players that can easily achieve this without installing any other software.
The output format
- GEM: Media files are protected by DRM. Only GemPlayer or its customization can recognize this file.
- EXE: Executable files are protected by DRM, the built-in media player.
Input format
- Video: MP4, AVI, MKV, WMV, MTS, RMVB, MXF, VOB, FLV, MPEG, TS and more.
- Audio: MP3, AAC, AC3, OGG, WMA and more.
- Images: JPG, BMP, PNG and more.
Screenshots:
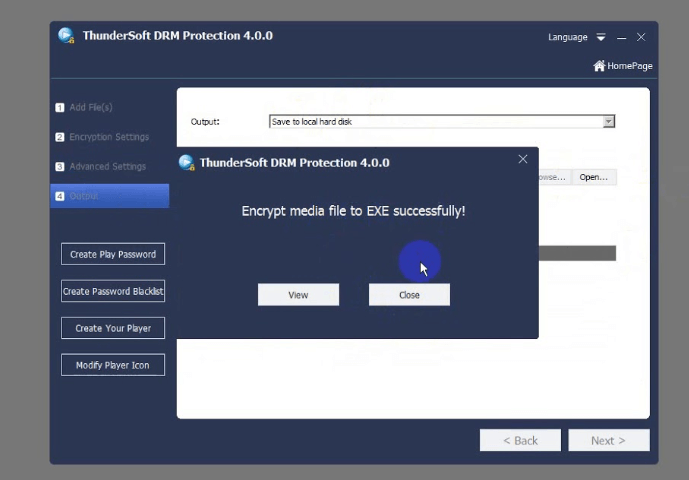
What’s New?
- Combine multiples and create a unique dome
- Encrypt multimedia content using highly advanced algorithms
- It encrypts at high speed and does not slow down when it meets the public.
- Ability to encrypt in different ways.
- Learn how to copy content using methods like screenshots.
- Ability to invalidate passwords online
- Quickly and easily generate passwords for multiple users
- Have a built-in player for smooth gameplay without installing additional software.
ThunderSoft DRM Protection Key:
- SWERTW6Y7UE8ID9FIJUYC6TR5S4RDFTDGFGV
- SWER5T6YE7U8DI9FOKVIJUYCT6R54ESRDFTDG
- DSWE4R5T6Y7U8EI9DOFKIJUY76TD5R4ERFFGB
- DSWERT6Y7EU8ID9OFKIJVUY76T5RD4RFTGERFG
You May Also Like:
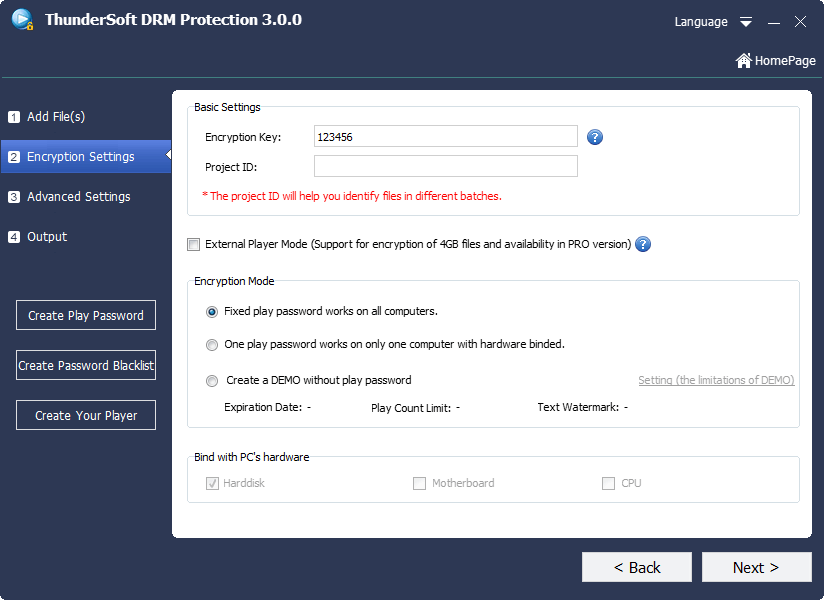
System Requirements:
- System: Windows 7 / Vista / 7/8/10
- RAM: Minimum 512 MB.
- HHD space: 100 MB or more.
- Processor:2 MHz or faster.
How to Install ThunderSoft DRM Protection Activation bypass?
- Download the software and run the installation file.
- Click “I Agree” to continue.
- Select the installation method and click “Next”.
- Change the installation folder and click “Next”.
- Select the components and click Install to start the installation.
- After setup is complete, click Close.
- Done! Enjoy it.
Download Link
#ThunderSoft #DRM #Protection #Activation bypass #Key #Free #Download



