GhostVolt Business Activation bypass + Activation Key Full Version Free Download
GhostVolt Business 2.43.24 Activation bypass employs cutting-edge encryption to safeguard your files, data, and folders, thwarting unauthorized access. Shield sensitive information by rendering it indecipherable to unauthorized parties, transforming it into a code accessible only to permitted users. Ensure the confidentiality and integrity of your data with this powerful encryption solution.
GhostVolt Business protects your files, data, and folders with advanced encryption to prevent unauthorized access, data breaches, and cybercrime. Only authorized users can access your data, keeping it secure and confidential.
Protect sensitive information with GhostVolt
File encryption is a way to protect sensitive information by making it unreadable to anyone who does not have permission to see it. This is done by converting your information into a secret code that only you and authorized people can unlock.
We provide you and your team with a completely secure on-site collaborative workspace. With GhostVolt, your business-critical data is automatically encrypted with the latest security standards. This allows you to not only comply with legal requirements but also protect your data from cyberattacks and malicious actors.
You can back up all your files, including medical records, photos, videos, tax returns, and other documents, so you can always control who has access to your files and data. All your files are automatically encrypted with industry-standard AES 256 encryption and it works just like a regular file manager, so you’ll already know how to use it.
This application brings files and folders to GhostVolt, where they are automatically encrypted. Only you can access your data. All others are denied access. Back up all your personal and business information, including photos, videos, credit card information, customer information, tax returns, and other documents.
Securely share files and data with friends, colleagues, and clients via cloud, email, or other sharing methods. Full integration with Microsoft OneDrive and Google Drive. Access your encrypted files in the cloud from any computer. Create, organize and keep your important personal notes secure using the built-in secure note editor.
GhostVolt Business Activation bypass is a comprehensive and secure solution that meets the complex needs of business environments in managing and protecting confidential information. As a robust encryption and data management platform, GhostVolt Business offers a variety of features to protect your critical data while ensuring compliance with various regulatory standards. The software’s intuitive interface makes it accessible to users with varying levels of technical knowledge and facilitates seamless implementation into an organization’s workflow.
One of the unique features of GhostVolt Business is its end-to-end encryption feature that provides a high level of security for your files and documents. This ensures data is protected at rest and in transit, reducing the risk of unauthorized access. This software uses AES-256 encryption, a strong and widely recognized encryption standard that further enhances the security of sensitive information.
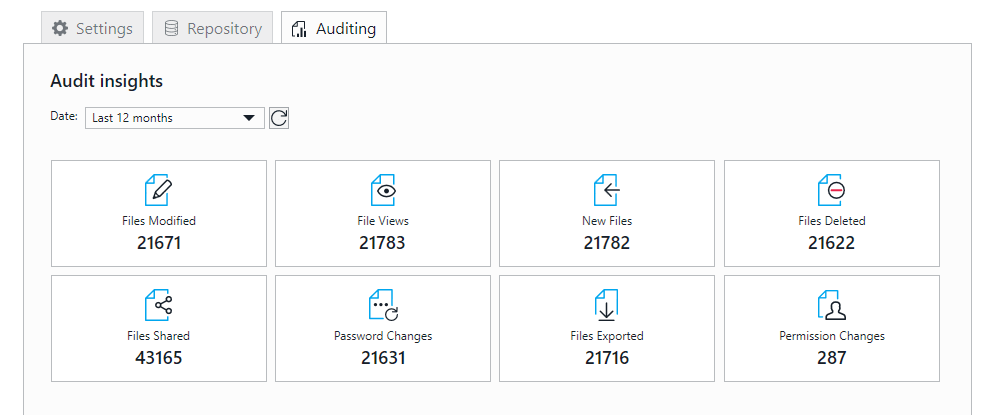
GhostVolt Business excels at user management with features that give administrators granular control over permissions. This includes the ability to assign roles, restrict access to specific folders, and manage user groups, providing a customized approach to data access within your organization. The software also includes activity monitoring and audit logging, allowing administrators to track user actions and file changes, improving accountability and compliance.
GhostVolt Business makes collaboration easier by enabling secure file sharing in business environments. Users can share encrypted files with colleagues while maintaining access controls and permissions. Additionally, the software integrates seamlessly with your existing cloud storage solutions to improve workflow efficiency. To ensure compliance with regulatory requirements, GhostVolt Business provides comprehensive reporting tools.
These tools can help you create audit reports, track changes, and ensure your encryption practices meet industry standards. This software is designed to help businesses comply with standards defined by regulations such as GDPR, HIPAA, and more. Additionally, GhostVolt Business provides version control and change management, allowing users to revert to previous versions of documents and track changes over time. This feature is important for maintaining data integrity and supporting collaboration in enterprise environments.
In short, GhostVolt Business Activation bypass is a powerful encryption and data management solution tailored to your business environment. With a focus on end-to-end encryption, user management, collaboration and compliance reporting, companies seeking to effectively protect sensitive data and comply with the dynamic regulatory standards that are today’s business environment have become an indispensable tool.
Features & Highlights:
- Encrypt and protect all your data
- Prevent unauthorized access to files and folders
- Prevent data breaches and leaks
- Regulatory compliance and legal compliance
- Secure collaboration of files, folders and data
- Access control to paper files and folders
- End-to-End Encryption: ghostvolt Business uses strong end-to-end encryption to ensure the security of your files and documents at rest and in transit.
- AES-256 Encryption Standard – This software uses the widely recognized and secure AES-256 encryption standard for added data protection.
- Intuitive Interface: ghostvolt Business has an intuitive interface aimed at users with a variety of technical skills.
- User Management: Administrators can manage user permissions at a granular level by assigning roles, restricting access to specific folders, and organizing users into groups.
- Activity Monitoring: The software includes activity monitoring and audit logs that allow administrators to monitor user actions and track file changes for greater accountability.
- Secure File Sharing: ghostvolt Business facilitates secure file sharing in enterprise environments while giving users control over access and permissions.
- Cloud Storage Integration: The software integrates seamlessly with your existing cloud storage solutions to streamline collaboration and improve workflow efficiency.
- Comprehensive reporting tools: ghostvolt Business provides reporting tools to create audit reports and ensure your encryption practices meet industry standards and regulatory requirements.
- Regulatory Compliance Support – The software is designed to help businesses comply with regulatory requirements such as GDPR, HIPAA, and other industry-specific standards.
- Version Control and Change Management: Version control and revision control capabilities allow users to revert to previous versions of a document and track changes over time.
- Secure Collaboration Space – ghostvolt Business provides a secure collaboration space where your team can work on projects while keeping your data safe.
- Customizable access controls: Administrators can customize access controls to ensure that users have the appropriate level of access to data based on their roles and responsibilities.
- File-level encryption: This software enables file-level encryption, providing an additional layer of security for individual documents.
- Multi-factor authentication (MFA): ghostvolt Business supports multi-factor authentication to improve the security of user authentication.
- Centralized Management Console – Administrators can efficiently manage all aspects of ghostvolt Business through a central management console.
- Folder-level permissions: Users can set folder-level permissions to allow or restrict access to specific sets of files.
- Remote data wipe: If a device is lost or stolen, administrators can remotely wipe sensitive data to prevent unauthorized access.
- Offline Access: Users can access encrypted files offline, providing flexibility in different work environments.
- Role-Based Access Control (RBAC) – The software supports role-based access control, which allows administrators to define roles and associated permissions for users.
- Secure Data Backup: ghostvolt Business includes a secure data backup feature that ensures the availability of critical information even in the event of data loss.
- Secure Document Preview: Users can securely preview encrypted documents without compromising data integrity.
- Granular Permission Settings: Administrators have granular control over permission settings, allowing them to finely configure permissions for different user roles.
- Automatic file encryption: The software can automatically encrypt files based on predefined rules or criteria, simplifying the encryption process.
- Shipping tracking: ghostvolt Business continually monitors and reports on your compliance status, helping you proactively meet regulatory standards.
- File access monitoring: Detailed file access monitoring provides insight into how users interact with sensitive data.
- Data expiration policies: Administrators can set data expiration policies to ensure that access to specific information is restricted within a time period.
- Password policy enforcement: The software enforces password policies to increase the security of user credentials.
- Cross-platform compatibility: ghostvolt Business is compatible with multiple operating systems and supports a variety of business environments.
- Client-side encryption: The software uses client-side encryption. This improves security by encrypting data on the user’s device before sending it.
Privacy
Encrypting data allows individuals and organizations to ensure the privacy of sensitive information and protect it from unauthorized access and misuse.
Data protection
By encrypting files, consumers and businesses reduce the risk of falling victim to cyberattacks that can cause data theft and financial loss.
Protection from identity theft
Even if your files are stolen, compromised, or hacked, their contents are protected and unreadable by hackers and criminals, preventing identity theft.
Prevent data theft
File encryption helps reduce the risk of data breaches that can lead to significant financial loss, reputational damage, and loss of customer trust.
Comply with
Encryption is often required by various regulatory standards such as HIPAA and PCI-DSS, which help businesses comply with legal and industry requirements.
Why GhostVolt?
- Uses AES-256 encryption
- No backdoors or private keys
- professionally tested
- Two-factor authentication
- It was involved in integration
What’s New?
Added:
- New audit event when a user is granted or denied access to a folder
- New audit event when a user’s resource access rights are changed.
Fixed:
- Fixed a bug where the installer created unnecessary UDP ports.
- Fixed a permissions bug that caused “File” to appear in the context menu for users without proper access rights.
- Turning the encryption key will reset all created thumbnails.
- Fixed a bug that allowed users with create folder access to create new folders and restrict other GhostVolt administrators.
- Fixed a security bug where file comment icons were displayed in File Explorer even for users who did not have access to file comments.
- The ability to extend tests now works as expected.
- Updated number of GhostVolt Enterprise trial users from 3 to 10
- Developers constantly update their projects. The latest software updates can be found on the official website.
GhostVolt Business Activation Key:
- AWER5T6Y7U8I9ODKJICHUGYFTDRS5TDF
- SER5T6Y7U8IDJIHGCFRDXST6Y7UDIUYTF
GhostVolt Business Product Key:
- ESR5T6Y7U8IDJIHUGYFTDR56TY7UDY7T6
- SER5T6Y78UDIJHUGCFDRS5T6Y7SUIDUHY
You May Also Like:
System Requirements:
- System: Windows 7 / Vista / 7/8/10
- RAM: Minimum 512 MB.
- HHD space: 100 MB or more.
- Processor:2 MHz or faster.
How to Install GhostVolt Business Activation bypass?
- Download the software and run the installation file.
- Click “I Agree” to continue.
- Select the installation method and click “Next”.
- Change the installation folder and click “Next”.
- Select the components and click Install to start the installation.
- After setup is complete, click Close.
- Done! Enjoy it.
#GhostVolt #Business #Activation bypass #Activation #Key #Download



